标签:tail get direct 部分 版本 防火 pass pos 命令
参考连接:<https://ceph.readthedocs.io/en/latest/radosgw/>;
? 作为文件系统的磁盘,操作系统不能直接访问对象存储。相反,它只能通过应用程序级别的API访问。Ceph是一种分布式对象存储系统,通过Ceph对象网关提供对象存储接口,也称为RADOS网关(RGW)接口,它构建在Ceph RADOS层之上。RGW使用librgw (RADOS Gateway Library)和librados,允许应用程序与Ceph对象存储建立连接。RGW为应用程序提 供了一个RESTful S3 / swift兼容的API接口,用于在Ceph集群中以对象的形式存储数据。Ceph还支持多租户对象存储,可以通过RESTful API访问。此外,RGW还支持Ceph管理API,可以使用本机API调用来管理Ceph存储集群。
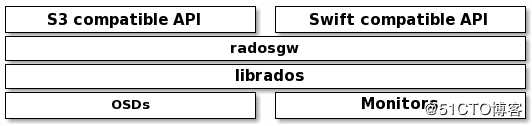
? 对于生产环境,建议您在物理专用机器上配置RGW。但是,如果您的对象存储工作负载不太大,您可以考虑将任何监视器机器作为RGW节点使用。RGW是一个独立的服务,它从外部连接到Ceph集群,并向客户端提供对象存储访问。在生产环境中,建议您运行多个RGW实例,由负载均衡器屏蔽。
? [本例以cephmanager01为例]
? 1)安装ceph-radosgw(需要安装的节点均需要安装)
[root@cephmanager01 ~]# yum -y install ceph-radosgw? 2)部署服务
? 进入cephuser的工作目录执行
[cephuser@cephmanager01 cephcluster]$ ceph-deploy rgw create cephmanager01? 3)确认部署成功
# 确认是否有rgw是active
[cephuser@cephmanager01 cephcluster]$ sudo ceph -s
# 确实7480端口是否开通
[cephuser@cephmanager01 cephcluster]$ sudo netstat -antulp |grep 7480
# 访问看是否有输出
[cephuser@cephmanager01 ~]$ sudo curl http://cephmanager01:7480
# 确认是否生成了rgw相关的pools
[cephuser@cephmanager01 ~]$ sudo ceph osd lspools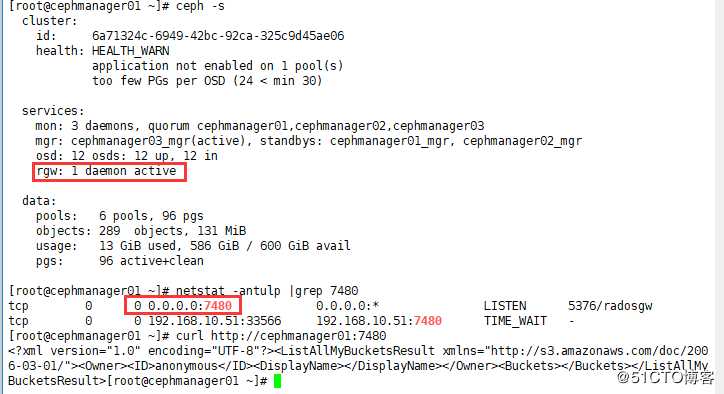
1)修改cephuser工作目录的配置文件ceph.conf
在 [global] 节后添加的内容如下:
#cephmanager01为gateway-node的节点名称,80为需要修改的端口
[client.rgw.cephmanager01]
rgw_frontends = "civetweb port=80"2)同步配置文件
将该配置文件推送到其他节点
[cephuser@cephmanager01 cephcluster]$ ceph-deploy --overwrite-conf config push cephmanager01 cephmanager02 cephmanager033)重启服务生效
[cephuser@cephmanager01 cephcluster]$ sudo systemctl restart ceph-radosgw.target4)确认是否成功
# 确实80端口是否开通
[cephuser@cephmanager01 cephcluster]$ sudo netstat -antulp |grep rados
# 访问看是否有输出
[cephuser@cephmanager01 ~]$ sudo curl http://cephmanager01:80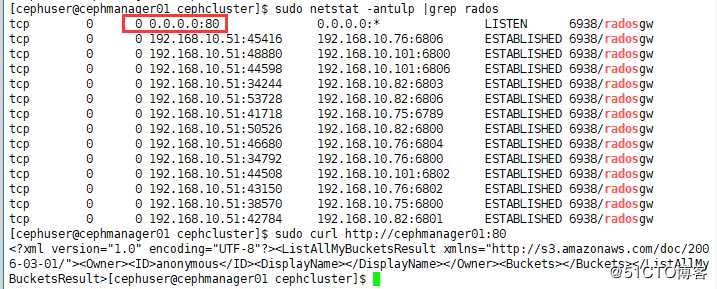
注:如果开启了防火墙,需要添加80端口的例外
# firewalld示例
[cephuser@cephmanager01 cephcluster]$ sudo firewall-cmd --list-all
[cephuser@cephmanager01 cephcluster]$ sudo firewall-cmd --zone=public --add-port 80/tcp --permanent
[cephuser@cephmanager01 cephcluster]$ sudo firewall-cmd --reload#创建 radosgw 用户
[root@cephmanager01 ~]# radosgw-admin user create --uid="radosgwuser" --display-name="radosgwuser demo"
#注意:请把 access_key 和 secret_key 保存下来,也可以通过命令获取
[root@cephmanager01 ~]# radosgw-admin user info --uid="radosgwuser"(1)官方给出了一个 Python脚本访问的案例
? 1)安装对应的软件包python-boto
# yum install python-boto -y? 2)修改脚本信息
# 需要修改access_key、secret_key、host、port、bucket名称等信息
# cat s3test.py
import boto.s3.connection
access_key = ‘B4TZNYMJ2VMUTF97BFS9‘
secret_key = ‘TpxrusS0f42yyYZNuvUni5Shoc9yJH83myWO5gCc‘
conn = boto.connect_s3(
aws_access_key_id=access_key,
aws_secret_access_key=secret_key,
host=‘192.168.10.51‘, port=80,
is_secure=False, calling_format=boto.s3.connection.OrdinaryCallingFormat(),
)
bucket = conn.create_bucket(‘my-new-bucket‘)
for bucket in conn.get_all_buckets():
print "{name} {created}".format(
name=bucket.name,
created=bucket.creation_date,
)? 3)执行脚本并确认
# python s3test.py
my-new-bucket 2020-07-03T02:45:31.174Z如果第一次创建bucket会生成一个default.rgw.buckets.index的pool,第一次向bucket里面防入数据,会生成一个default.rgw.buckets.data的pool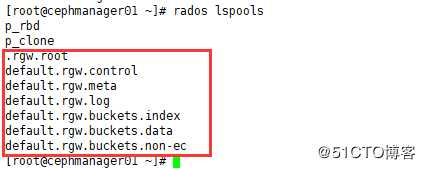
(2)s3cmd访问
? 1)安装 s3cmd 客户端
# yum install s3cmd -y? 2)生成一个配置文件,在当前目录下,输入生成的key
# s3cmd --configure
Enter new values or accept defaults in brackets with Enter.
Refer to user manual for detailed description of all options.
Access key and Secret key are your identifiers for Amazon S3. Leave them empty for using the env variables.
Access Key [UTCFB8H59AF611EYFYDY]: B4TZNYMJ2VMUTF97BFS9 #需要输入radosgwuser的Access Key
Secret Key [R7DdzYzn7llNlwiLC8FtZEs2vfNlEBBQFBFaxRUb]: TpxrusS0f42yyYZNuvUni5Shoc9yJH83myWO5gCc #需要输入radosgwuser的Secret Key
Default Region [US]: #保持默认,注:国家只支持US
Use "s3.amazonaws.com" for S3 Endpoint and not modify it to the target Amazon S3.
S3 Endpoint [cephnode01]: 192.168.10.51:80 #输入rgw的ip和端口
Use "%(bucket)s.s3.amazonaws.com" to the target Amazon S3. "%(bucket)s" and "%(location)s" vars can be used
if the target S3 system supports dns based buckets.
DNS-style bucket+hostname:port template for accessing a bucket [%(bucket)s.cephnode01.donghai.com]: 192.168.10.51:80/%(bucket)s #输入rgw的ip和端口,注意格式
Encryption password is used to protect your files from reading
by unauthorized persons while in transfer to S3
Encryption password: #启用加密
Path to GPG program [/usr/bin/gpg]:
When using secure HTTPS protocol all communication with Amazon S3
servers is protected from 3rd party eavesdropping. This method is
slower than plain HTTP, and can only be proxied with Python 2.7 or newer
Use HTTPS protocol [No]: no #是否启用https
On some networks all internet access must go through a HTTP proxy.
Try setting it here if you can‘t connect to S3 directly
HTTP Proxy server name: #是否设置代理
New settings:
Access Key: B4TZNYMJ2VMUTF97BFS9
Secret Key: TpxrusS0f42yyYZNuvUni5Shoc9yJH83myWO5gCc
Default Region: US
S3 Endpoint: 192.168.10.51:80
DNS-style bucket+hostname:port template for accessing a bucket: 192.168.10.51:80/%(bucket)s
Encryption password:
Path to GPG program: /usr/bin/gpg
Use HTTPS protocol: False
HTTP Proxy server name:
HTTP Proxy server port: 0
Test access with supplied credentials? [Y/n] y #测试访问
Please wait, attempting to list all buckets...
Success. Your access key and secret key worked fine :-)
Now verifying that encryption works...
Not configured. Never mind.
Save settings? [y/N] y #保持配置
Configuration saved to ‘/root/.s3cfg #配置保持路径? 3)bucket相关操作
#查看bucket
# s3cmd ls
# 创建test-bucket
# s3cmd mb s3://test-bucket
ERROR: S3 error: 403 (SignatureDoesNotMatch)
#正对找个错误,需要在配置文件/root/.s3cfg启用signature_v2 = True
#上传单个文件,上传目录需要用递归方式--recurisve
# s3cmd put /etc/hosts s3://test-bucket/57_hosts
#查看test-bucket里面存放的文件
# s3cmd ls s3://test-bucket
#从test-bucket下载文件,并确认当前目录是否有57_hosts_57文件
# s3cmd get s3://test-bucket/57_hosts 57_hosts_57
#删除文件
# s3cmd rm s3://test-bucket/57_hostsswift用户是在现有用户基础上创建子用户
# 查看现有用户
[root@cephmanager01 ~]# radosgw-admin user list
# 创建swift api子用户
[root@cephmanager01 ~]# radosgw-admin subuser create --uid=radosgwuser --subuser=radosgwuser:swift --access=full
# --access赋予权限,避免权限问题
#结果注意swift_keys的secret_key,部分版本需要新建生成1)安装python-setuptools和pip
# yum install python-setuptools
# yum install python-pip -y
# 升级python-swiftclient
# pip install --upgrade python-swiftclient
# 如果源有问题,可以选择阿里云的源
# pip install --upgrade python-swiftclient -i http://mirrors.aliyun.com/pypi/simple/ --trusted-host mirrors.aliyun.com
# 确认swift版本
# swift --version2)查看验证
# 查看,注意ip、port、用户名和密钥,确认输出了其他bucket
# swift -A http://192.168.10.51:80/auth/1.0 -U radosgwuser:swift -K ‘7pqD1mRdOBCm19WO5t7njgKGezEhF2tmepSY8YoZ‘ list3)配置环境变量
每次输入用户名密钥ip等信息比较麻烦,建议设置环境变量
# swift list #会提示你需要定义那些变量
# cat swift_openrc
export ST_AUTH=http://192.168.10.51:80/auth
export ST_USER=radosgwuser:swift
export ST_KEY=7pqD1mRdOBCm19WO5t7njgKGezEhF2tmepSY8YoZ
# source swift_openrc4)其他相关操作
# 新建
# swift post test-swift
# 上传文件或目录
# swift upload test-swift /etc/host
# 查看上传文件内容
# swift list test-swift
# 下载
# swift download test-swift etc/hosts
# 删除
# swift delete test-swift etc/hosts标签:tail get direct 部分 版本 防火 pass pos 命令
原文地址:https://blog.51cto.com/14758677/2508539