标签:
在当今互联网时代,数据越来越来重要。那么如何加密?解密?以及通过什么方式来认证了??
接下来,我就会和大家谈谈加密,解密以及CA签证的实现。
首先大家的知道一些加密,解密的基本常识:
[root@stu21 ~]# openssl rand -base64 12
v8qA8lKAa19aZAWV
?
我直接把对称加密以及非对称加密以图片显示:
?
下面来说下何谓对称加密,非对称加密(公钥加密),单向加密
?
1、加密方和解密方使用同一个密钥。
2、加密解密的速度比较快,适合数据比较长时的使用。
3、密钥传输的过程不安全,且容易被破解,密钥管理也比较麻烦。
4、加密算法:DES(Data Encryption Standard)、3DES、AES(AdvancedEncryption Standard,支持128、192、256、512位密钥的加密)、Blowfish。
5、加密工具:openssl、gpg(pgp工具)
二.非对称加密(公钥加密):
1、每个用户拥用一对密钥加密:公钥和私钥。
2、公钥加密,私钥解密;私钥加密,公钥解密。
3、公钥传输的过程不安全,易被窃取和替换。
4、由于公钥使用的密钥长度非常长,所以公钥加密速度非常慢,一般不使用其去加密。
5、某一个用户用其私钥加密,其他用户用其公钥解密,实现数字签名的作用。
6、公钥加密的另一个作用是实现密钥交换。
7、加密和签名算法:RSA、ELGamal。
8、公钥签名算法:DSA。
9、加密工具:gpg、openssl
?
三.单向加密:
1、特征:雪崩效应、定长输出和不可逆。
2、作用是:确保数据的完整性。
3、加密算法:md5(标准密钥长度128位)、sha1(标准密钥长度160位)、md4、CRC-32
4、加密工具:md5sum、sha1sum、openssldgst。
5、计算某个文件的hash值,例如:md5sum/shalsum?FileName,openssl dgst–md5/-sha1 FileName。
?
下面我就来谈谈openssl是什么?如何实现CA自签证?
openssl:
1)组件:libcrypto:加密库。
libssl:实现ssl功能的库。
openssl:多用途的加密工具,能够提供对称加密、公钥加密、单向加密,且可以作为一个简单的本地CA用。
2)openssl的主配置文件:/etc/pki/tls/openssl.cnf
使用openssl实现私有CA
建立私有CA(如下是实现的具体步骤)
????????????[root@stu31 ~]# cd /etc/pki/tls
????????????
????????????[root@stu31 tls]# ls
????????????cert.pem certs misc openssl.cnf private
????????????
????????????[root@stu31 tls]# vim openssl.cnf
????????????
????????????[root@stu31 tls]# cd ..
????????????
????????????[root@stu31 pki]# ls
????????????CA ca-trust java nssdb rpm-gpg rsyslog tls
????????????
????????????[root@stu31 pki]# cd CA/
????????????
????????????[root@stu31 CA]# ls
????????????certs crl newcerts private
????????????
????????????[root@stu31 CA]# (umask 077;openssl genrsa -out private/cakey.pem 2048)
????????????Generating RSA private key, 2048 bit long modulus
????????????.......................................................................................................................................................+++
????????????.................................+++
????????????e is 65537 (0x10001)
????????????[root@stu31 CA]# ls
????????????certs crl newcerts private
????????????
????????????[root@stu31 CA]# ls -l private/
????????????total 4
????????????-rw-------. 1 root root 1679 Dec 4 15:00 cakey.pem
????????????[root@stu31 CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem
????????????You are about to be asked to enter information that will be incorporated
????????????into your certificate request.
????????????What you are about to enter is what is called a Distinguished Name or a DN.
????????????There are quite a few fields but you can leave some blank
????????????For some fields there will be a default value,
????????????If you enter ‘.‘, the field will be left blank.
????????????-----
????????????Country Name (2 letter code) [CN]:
????????????State or Province Name (full name) [Beijin]:
????????????Locality Name (eg, city) [Beijin]:
????????????Organization Name (eg, company) [ChangSheng]:
????????????Organizational Unit Name (eg, section) []:OD
????????????Common Name (eg, your name or your server‘s hostname) []:ca.changsheng.com
????????????Email Address []:1210982521@qq.com
????????????
????????????[root@stu31 CA]# ls
????????????cacert.pem certs crl newcerts private
????????????
????????????[root@stu31 CA]# touch index.txt
????????????
????????????[root@stu31 CA]# touch serial
????????????
????????????[root@stu31 CA]# echo 01 >serial
?
?
?
查看证书中的相关信息
????????????# openssl x509 -in /path/to/somefile.crt -noout -text|-subject|-serial
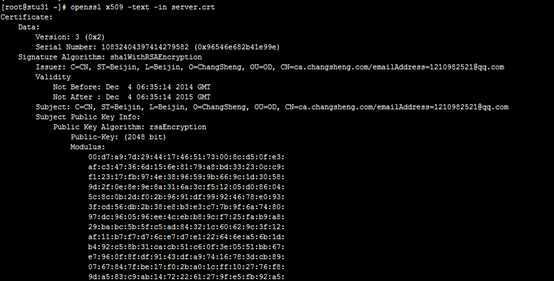
????
?
假如在同一台主机上,:用httpd服务自己给自己签证,具体步骤如下:
? ?
[root@stu31 ~]# cd /etc/httpd
[root@stu31 httpd]# ls
conf conf.d logs modules run
[root@stu31 httpd]# mkdir ssl
[root@stu31 httpd]# cd ssl/
[root@stu31 ssl]# pwd
/etc/httpd/ssl
? ?
[root@stu31 ssl]# (umask 077;openssl genrsa -out httpd.key 1024) //创建密钥
Generating RSA private key, 1024 bit long modulus
...++++++
.............++++++
e is 65537 (0x10001)
[root@stu31 ssl]# cat httpd.key
-----BEGIN RSA PRIVATE KEY-----
MIICXAIBAAKBgQDPtEGh9bGrkPrW+GNlmI/qBG5ggjAJwl3HOVcof/PkXq771LH/
EV28TvlQexZCnUnz/IeFesJKBZR6YmXB/bEm+gliRjBIXrzJ7j8hRa3L86foFFqw
dm98ID8Ix5RKNDb0QKAz8mk7urn8DsOzaNT2kq9VunbvpTOUI8cErLXdoQIDAQAB
AoGAOO+Tsj70hjBG4pjSPm5UvPScAS6O1o4GQO9x+fMhOy/NTdEfPelXxZ/sbehf
0MDnHc/Son9lNP9UlTvV4xiU77ighV90Dq/mOB9yVEVKHfqDgeiBRb7vuE/wvkkY
QPREJtbZBAboUredUmZ4MBB/+VYd/9/UaMzP+SAL5JWIpQECQQD1H2MUnEYzfn00
j0YzLcvp2jSpMoFSban4WXOeoz7CIhM7GLLuKVaWYlxNgREv7aDDVUzh0M1Un8I+
2hvXIF9RAkEA2OvK1vw3WavEcZq2f4VMHBRJ+7ECJpDCKHOmt9iw3ZwqlGpZs78q
o8di0z/j3KYoiWE3ddJXtMH2Sczo0GElUQJAENHbiaGDi6sFSmL+bSqaUGyhqm6F
wzM1M45nyZ3oA4g1C5wRQxhhEaakMMlHdaN3oY+r297pCAKCYK+0s1lMUQJAGpC1
5KI6vRaWFjuWQgO3EHFDpjlFRCfSP1X6guVcs6ceZ9Kmbabpt+kBJ1HZu/n1WO24
9wrthsuCOAOKN4rOIQJBAIBO36adQB2E1KI5VkxrlTc1snvTscTgiuowtM1gJUaL
aG/xT+1XYWpOWircRnH0d8dmGFajBF/EZpddoGX83jQ=
-----END RSA PRIVATE KEY-----
? ?
? ?
[root@stu31 ssl]# openssl req -new -key httpd.key -out httpd.csr //请求签证
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.‘, the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [Beijin]:
Locality Name (eg, city) [Beijin]:
Organization Name (eg, company) [ChangSheng]:
Organizational Unit Name (eg, section) []:OD
Common Name (eg, your name or your server‘s hostname) []:changsheng
Email Address []:1210982521@qq.com
? ?
Please enter the following ‘extra‘ attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
[root@stu31 ssl]# ls
httpd.csr httpd.key
[root@stu31 ssl]# openssl ca -in httpd.csr -out httpd.crt -days 365 //开始签证
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Dec 4 07:33:59 2014 GMT
Not After : Dec 4 07:33:59 2015 GMT
Subject:
countryName = CN
stateOrProvinceName = Beijin
organizationName = ChangSheng
organizationalUnitName = OD
commonName = changsheng
emailAddress = 1210982521@qq.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
DD:96:A4:9F:9F:E0:3F:5D:AB:53:34:CA:FB:A8:4B:86:E9:EB:7B:99
X509v3 Authority Key Identifier:
keyid:64:E5:92:A2:63:25:7A:66:04:4C:A4:FB:8D:F5:0C:D3:89:CA:AC:EC
? ?
Certificate is to be certified until Dec 4 07:33:59 2015 GMT (365 days)
Sign the certificate? [y/n]:y
? ?
? ?
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@stu31 ssl]# ll
total 12
-rw-r--r--. 1 root root 3865 Dec 4 15:34 httpd.crt
-rw-r--r--. 1 root root 696 Dec 4 15:33 httpd.csr
-rw-------. 1 root root 887 Dec 4 15:28 httpd.key
[root@stu31 ssl]# cd /etc/pki/CA
[root@stu31 CA]# cat index.txt //查看数据库
V????????151204073359Z????????????????01????????unknown????????/C=CN/ST=Beijin/O=ChangSheng/OU=OD/CN=changsheng/emailAddress=1210982521@qq.com
[root@stu31 CA]# cat serial
02
? ?
标签:
原文地址:http://www.cnblogs.com/na2po2lun/p/4191153.html