标签:
参考:
http://www.cnblogs.com/caoguoping100/p/3654452.html
https://wiki.wireshark.org/NullLoopback
抓包安装 Terminal终端,输入命令。
tcpdump -i pdp_ip0 -s 0 -w pdp.pcap 获取的报文,发现存在Loopback 。
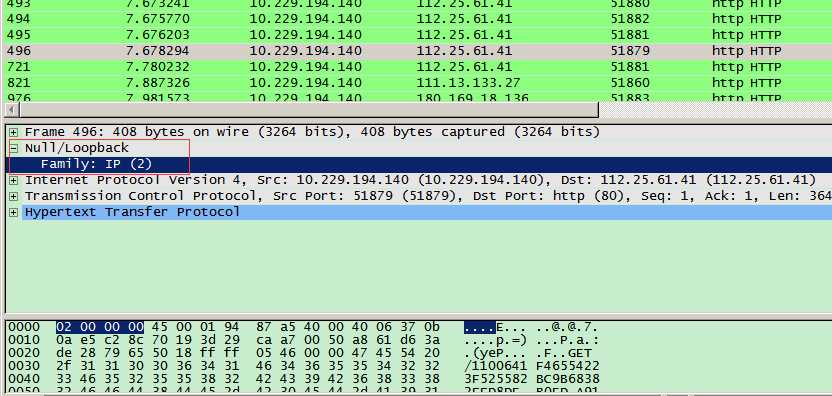
pdp_ip0 是3G/4G下的网卡,获取的报文直接loopback层。不解?
附wireshark解析
The "null" protocol is the link-layer protocol used on the loopback device on most BSD operating systems. It is somewhat misnamed, in that the link-layer header isn‘t "null" in the sense that there isn‘t any link-layer header; instead, the link-layer header is a 4-byte integer, in the native byte order of the machine on which the traffic is captured, containing an "address family"/"protocol family" value for the protocol running atop the link layer, for example AF_INET for IPv4 and AF_INET6 for IPv6. AF_INET is 2 on all BSD-based operating systems, as it was introduced at the same time the BSD versions with networking were released; however, AF_INET6, unfortunately, has different values in {NetBSD,OpenBSD,BSD/OS}, {FreeBSD,DragonFlyBSD}, and {Darwin/Mac OS X}, so an IPv6 packet might have a link-layer header with 24, 28, or 30 as the AF_ value.
The byte order is that of the host on which the packet was captured, so the dissector has to be able to handle both big-endian and little-endian values.
The "loopback" protocol is used by recent versions of OpenBSD; it‘s the same as the "null" protocol, except that the 4-byte AF_ value is in network byte order (big-endian) rather than host byte order.
The "null" protocol dates back to the original BPF implementation on BSD.
The "null" and "loopback" protocols are the lowest software layers, so they only depend on the implementation of the loopback device.
标签:
原文地址:http://www.cnblogs.com/iclk/p/4495163.html