标签:
Jenkins支持多种安全模型,并且能够与多种用户存储库集成。
Jenkins的安全配置:
系统设置→Configure Global Security
访问的页面为http://my.jenkins.server/configureSecurity/
勾选启用安全的复选框就可以在Jenkins中设置基本的安全。

Jenkins访问控制分为:安全域(即认证)与授权策略。
安全域决定Jenkins在认证的过程中从哪里寻找用户,默认包括的选项有:Jenkins专有用户数据库,LDAP,Servlet容器代理。
授权策略决定用户登录后可以做什么,默认包括的选项有:任何用户可以做任何事(没有任何限制),安全矩阵,登录用户可以做任何事情,遗留模式,项目矩阵授权策略。
说明:安全矩阵和项目矩阵授权策略的配置是一模一样的,唯一的区别是项目矩阵授权策略支持在Job的配置页面再次配置授权策略。
此外,还有一系列认证和用户管理相关的插件:
https://wiki.jenkins-ci.org/display/JENKINS/Plugins#Plugins-Authenticationandusermanagement
例如:通过Active Directory Plugin可以使用Microsoft Active Directory(即windows域账号)来进行认证,通过Crowd Plugin可以使用Atlassian Crowd来进行认证 ……
此外,如果没有可用的插件,Script Security Realm Plugin允许你使用自定义的脚本进行认证。
对于授权策略,除了默认的安全矩阵和项目矩阵授权策略,
Role Strategy Plugin提供了基于角色的授权策略,它允许你定义全局的和项目即的角色,并为用户分配相应角色。
关于用户的权限,作如下说明:
这一系列权限被分成几个组:Overall,Credentials,Slave,Job,Run,View,SCM
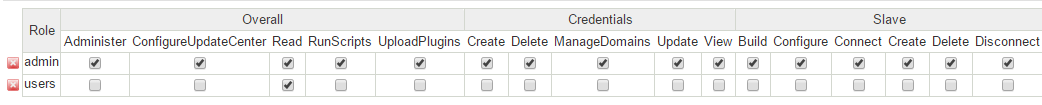

Overall:This group covers basic system-wide permissions:
Administer:Lets a user make system-wide configuration changes and other sensitive operations, for example in the main Jenkins configuration pages. This should be reserved for the Jenkins administrator.
ConfigureUpdateCenter
Read:This permission provides read-only access to virtually all of the pages in Jenkins. If you want anonymous users to be able to view build jobs freely, but not to be able to modify or start them, grant the Read role to the special “anonymous” user. If not, simply revoke this permission for the Anonymous user. And if you want all authenticated users to be able to see build jobs, then add a special user called “authenticated”, and grant this user Overall Read permission.
RunScripts:Required for running scripts inside the Jenkins process, for example via the Groovy console or Groovy CLI command.
UploadPlugins
Credentials
Create
Delete
Manage Domains
Update
View
Slave:This group covers permissions about remote build nodes, or slaves:
Build: This permission allows users to run jobs as them on slaves.
Configure: This permission allows users to configure slaves.
Connect: This permission allows users to connect slaves or mark slaves as online.
Create: This permission allows users to create slaves.
Delete: This permission allows users to delete existing slaves.
Disconnect: This permission allows users to disconnect slaves or mark slaves as temporarily offline.
Job:This group covers job-related permissions:
Build: This permission grants the ability to start a new build.
Cancel: This permission grants the ability to cancel a scheduled, or abort a running, build.
Configure: Change the configuration of a job.
Create:Create a new job.
Delete: Delete a job.
Discover:This permission grants discover access to jobs. Lower than read permissions, it allows you to redirect anonymous users to the login page when they try to access a job url. Without it they would get a 404 error and wouldn‘t be able to discover project names.
Read:This permission grants read-only access to project configurations. Please be aware that sensitive information in your builds, such as passwords, will be exposed to a wider audience by granting this permission.
Workspace:This permission grants the ability to retrieve the contents of a workspace.Jenkins checked out for performing builds. If you don‘t want a user to access files in the workspace (e.g. source code checked out from SCM or intermediate build results) through the workspace browser, you can revoke this permission.
Run:This group covers rights related to particular builds in the build history:
Delete:Delete a build from the build history.
Update:Update the description and other properties of a build in the build history. This can be useful if a user wants to leave a note about the cause of a build failure, for example.
View:This group covers managing views:
Configure: This permission allows users to change the configuration of views.
Create:This permission allows users to create new views.
Delete: This permission allows users to delete existing views.
Read: This permission allows users to see views (implied by generic read access).
SCM:Permissions related to your version control system:
Tag:Create a new tag in the source code repository for a given build.
审计——跟踪用户的行为
除了配置用户的帐号和访问权限,跟踪用户的操作也是有用的。
这里有两个插件可以帮助你做这样的事情:
Audit Trail plugin将用户的更改记录在一个特殊的日志文件中,
JobConfigHistory plugin允许你保存Jenkins系统配置和Job配置文件以前版本的副本。
参考:
《the jenkins definitive guide》
标签:
原文地址:http://my.oschina.net/donhui/blog/424980