标签:des style blog code http tar
A virtual machine (VM) architecture logically partitions a physical machine, such that the underlying hardware of the machine is time-shared and appears as one or more independently operation virtual machines. A computer platform in a virtual machine environment may comprise a virtual machine monitor (VMM) that may create a plurality of virtual machines and runs on the computer platform to facilitate for other software the abstraction of one or more virtual machines.
A homogeneous virtualization platform may comprise a plurality of virtual machines in which all of the virtual machines comply with host system architecture that the underlying hardware machine supports. The term ‘system architecture‘ may comprise a set of registers, data structures, and instructions designed to support basic system-level operations such as memory management, interrupt and exception handling, task management and control of multiple processors, possibly other tasks.
An embodiment of a computer system?1000?supporting a heterogeneous virtualization technology is shown in FIG. 1. A non-exhaustive list of examples for the computer system?1000?may include mainframe computer, mini-computer, personal computer, portable computer, laptop computer and other devices for transceiving and processing data. The computer system?1000?may comprise a heterogeneous virtualization platform?1001?and underlying hardware machine?1002?supporting virtualization technology. The underlying hardware machine?1002?may be setup in compliance with host system architecture. Examples for the host system architecture may comprise a 64-bit system architecture such as Intel? Itanium? system architecture, Intel? Pentium-M? system architecture and Intel? Xeon? system architecture, and possibly other system architecture.
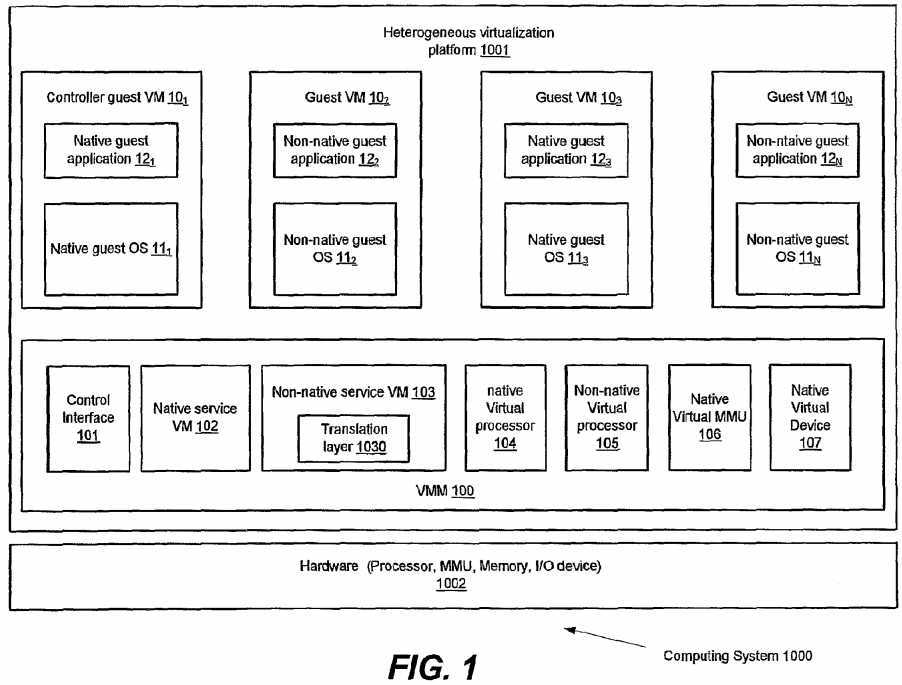
The heterogeneous virtualization platform?1001?may comprise a virtual machine monitor?100?providing the virtualization capability on top of the hardware machine?1002?and a plurality of guest virtual machines?101-10N?created by the virtual machine monitor?100. Examples for the guest virtual machines may comprise modified guest virtual machine and unmodified guest virtual machine.
The plurality of guest virtual machines?101-10N?may run their own operating systems and application software. In the heterogeneous virtualization platform?1001?as shown in FIG. 1, at least one of the guest virtual machines?101-10N?(e.g., guest virtual machine?101?and?103) may comprise a native guest operating system (e.g., native guest OS?111?and?113) and a native guest application (e.g., native guest application?121?and?123) that support a guest system architecture native to the host system architecture, while at least one of the guest virtual machines?101-10N?(e.g., guest virtual machine?102?and?10N) may comprise a non-native guest operating system (e.g., native guest OS?111?and?113) and a non-native guest application that support another guest system architecture non-native to the host system architecture. However, it should be appreciated that other embodiments may implement other technologies for the structure of the heterogeneous virtualization platform, for example, all of the guest virtual machines support non-native guest system architectures different from the host system architecture. Examples for the non-native guest system architecture may comprise a 32-bit system architecture such as Intel? x86 system architecture, Sun? SPARC? system architecture, and IBM? Power? system architecture, and possibly other system architecture.
In the embodiment shown in FIG. 1, the guest virtual machine?101?may be used to control other guest virtual machines?102-10N, and therefore, may be further called as a controller guest virtual machine?101. For example, the controller guest virtual machine?101?may control device-related operations for other guest virtual machines.
The virtual machine monitor?100?may comprise a control interface?101, a native service virtual machine?102, a non-native service virtual machine?103, a native virtual processor?104, a non-native virtual processor?105, a native virtual memory management unit (MMU)?106, a native virtual device?107?and possibly other components.
The control interface?101?may be a user interface that may provide BIOS interface and data to the service virtual machines?102?and?103.
The native service virtual machine?102?may facilitate execution of a native guest operating system (e.g., native guest OS?111) supporting the guest system architecture native to the host system architecture, and manage the virtualization of system resources for the native guest operating system at runtime. The native service virtual machine?102?may intercept an operating system boot loader, an interrupt handler, input/output, privileged Instructions and procedures dynamically through modifying runtime codes or back-patching.
The non-native service virtual machine?103?may facilitate execution of a non-native guest operating system (e.g. non-native guest OS?112) supporting a guest system architecture non-native to the host system architecture, and manage the virtualization of system resources for the non-native guest operating system at runtime. Similarly with the native service virtual machine?102, the non-native service virtual machine?103?may intercept an operating system boot loader, an interrupt handler, input/output, privileged instructions and procedures dynamically through modifying runtime codes or back-patching.
In the embodiment, the non-native service virtual machine?103?may further comprise a translation layer?1030?to translate instructions from the non-native guest operating system complying with the non-native guest system architecture into instructions to be executed by the underlying hardware machine?1002?complying with the host system architecture and further facilitate virtualization environment for execution of the non-native guest operating system.
Since the translation layer loaded in the non-native service virtual machine?103?runs in a privileged level as the non-native service virtual machine?103?does (i.e., host ring level?0), the translation layer?1030?may be further provided with privileged instructions supporting privileged operations for accessing the system resources, such as control registers, debug registers, performance monitor unit, timer, interrupts, and possibly other resources. The translation layer may be further provided with data structures supporting the system resources that the privileged instructions may be able to access. For example, if the non-native guest system architecture is a 32-bit system architecture, the translation layer may comprise a 32-bit execution layer integrated with the above-described privileged instructions and data structures.
The native virtual processor?104?may fulfill virtualization of a processor supporting the host system architecture and the non-native virtual processor?104?may fulfill virtualization of a processor supporting the non-native guest system architecture. When stop or resume a guest operating system, the native virtual processor?104or the non-native virtual processor?105?may save/restore native processor states or non-native processor states presented to the guest operating system. In the heterogeneous virtualization platform?1001, the underlying hardware processor may operate complying with the host system architecture and present native processor states, therefore, the translation layer?1030?may be responsible for mapping between the non-native processor states and native processor states in order to facilitate processor virtualization for execution of the non-native guest operating system.
The native virtual memory management unit (MMU)?106?may be responsible for emulating a native memory model for the guest operating systems, including address space assignment, virtual address translation, page table management, and so on. More specifically, the native virtual MMU?106?may translate native logical address supporting the host system architecture into native physical address, and maintain a native page table comprising the native physical address for each memory page complying with the host system architecture. In the heterogeneous virtualization platform?1001, the non-native guest operating system may maintain a non-native page table comprising the non-native physical address for each memory page complying with the non-native guest system architecture. Therefore, the translation layer?1030?may be further responsible for mapping between the non-native physical address in the non-native guest operating system and the native physical address in the virtual machine monitor in order to facilitate memory virtualization for execution of the non-native guest operating system.
The native virtual device?107?may fulfill virtualizations of devices for I/O operations in the guest operating systems. The native virtual device?107?may further support a native memory mapped I/O complying with the host system architecture, wherein the native memory mapped I/O may represent a native memory address of an entry of a special memory page that may store device ports in its entries. In the heterogeneous virtualization platform?1001, in order to facilitate device virtualization for execution of the non-native guest operating system that may execute either a non-native memory mapped I/O instruction or a non-native I/O instruction complying with the non-native guest system architecture for the I/O operation, the translation layer?1030?may be further responsible for mapping the non-native I/O instruction or the non-native memory mapped I/O instruction with the native memory mapped I/O instruction.
Other embodiments may implement other technologies for the structure of the heterogeneous virtualization system of FIG. 1. For example, the translation layer?1030?may support different non-native guest operating systems complying with different non-native guest system architectures. In such case, the translation layer may be provided with different capsules supporting instruction translation from the different guest system architectures to the host system architecture.
FIG. 2 shows an embodiment of a method of launching a guest operating system in the heterogeneous virtualization platform of FIG. 1.
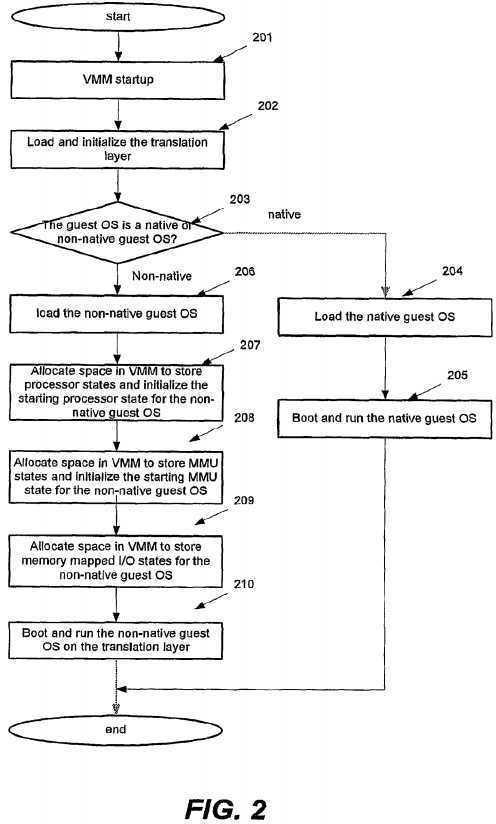
In block?201, the virtual machine monitor?1oo may start up and run at a privileged level (e.g., host ring?0) in the heterogeneous virtualization platform?1001. In block?202, user or any suitable device may load and initialize the translation layer?1030?in the virtual machine monitor?100. For example, the translation layer?1030may be loaded in the non-native service virtual machine?103?of the virtual machine monitor?100, or other suitable places in the virtual machine monitor.
In block?203, the virtual machine monitor?100?or other suitable device may determine whether the guest operating system to be launched is a native guest operating system supporting native guest system architecture or non-native guest operating system supporting non-native guest system architecture. In response to a native guest operating system, the user or other suitable device may load the native guest operating system over the virtual machine monitor (block?204) and boot the native guest operating system to run at a de-privileged level (e.g., guest ring O) (block?205).
In response to non-native guest operating system, the user or other suitable device may load the non-native guest operating system over the virtual machine monitor (block?206) and call the virtual machine monitor?100?to implement the following blocks in order to launch the non-native guest operating system.
In block?207, the virtual machine monitor?100?may allocate space to store processor states for the non-native guest operating system and initialize the starting processor state. In the embodiment, the translation layer?1030?may map the non-native processor states into native processor states and extra processor states, and maintain a copy of the mapped processor states for the non-native guest operating system in the allocated space. Examples for the processor states may comprise the general registers, floating point registers, various kinds of control registers and flag or status registers. More details on mapping of the processor states would be given later with reference to FIGS. 3-4.
In block?208, the virtual machine monitor?100?may allocate space to store MMU states for the non-native guest operating system and initialize the starting MMU state. In the embodiment, the translation layer?1030?may maintain a copy of MMU states for the non-native operating system in the allocated space. Examples for the MMU states may comprise data structures to map a non-native memory address complying with the non-native guest system architecture into a native memory address complying with the host system architecture, a page table complying with the host system architecture, and possibly other MMU states. More details on mapping of the memory addresses would be given later with reference of FIGS. 5-7.
In block?209?the virtual machine monitor?100?may allocate space to store memory mapped I/O states for the non-native guest operating system and initialize the starting memory mapped I/O state. In the embodiment, the translation layer?1030?may maintain a copy of memory mapped I/O states for the non-native guest operating system in the allocated space. The memory mapped I/O states may comprise a memory page complying with the host system architecture that may store device ports in its entries, and memory address of each entry may represent each corresponding memory mapped I/O. Then, the translation layer?1030?may be further responsible for translating non-native guest I/O instructions or non-native guest memory mapped I/O instructions from the non-native guest operating system into native memory mapped I/O instructions, which may be further discussed in more details with reference to FIGS. 8-9.
In block?210, the virtual machine monitor?100?or other suitable device may boot the non-native guest OS to run on the translation layer?1030.
Other embodiment may implement other technologies of launching the operating system. For example, if one of the guest operating systems?111-11N?is used to manage device-related operations for other guest operating systems (for example, the native guest operating system?111?of the controller guest virtual machine101), this guest operating system may be launched first, and device-related data for the other operating systems may be registered in this guest operating system when launching the other guest operating systems. For another example, the virtual machine monitor?100?may load the translation layer?1030?when finding that a guest operating system supporting the non-native guest system architecture runs on the top of it.
An embodiment of mapping non-native processor states complying with the non-native guest system architecture by the translation layer?1030?is shown in FIG. 3.
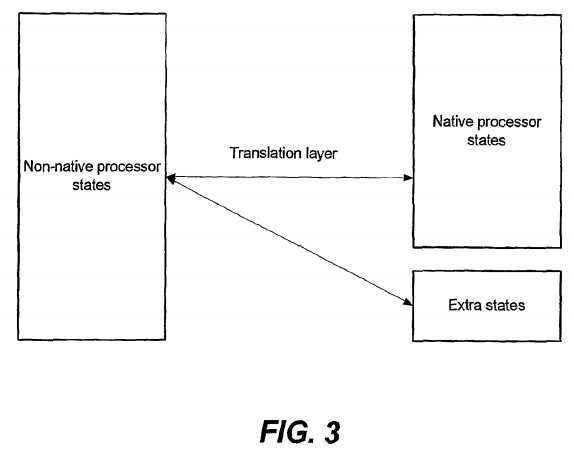
As depicted, the translation layer?1030?may map non-native processor states of the non-native virtual processor?105?into native processor states of the native virtual processor?104. However, there is possibility that not all of the non-native processor states can be mapped with the native processor states. In such case, the translation layer?1030?may keep the non-native processor states that may not be mapped with the native processor states in the memory as extra states. Therefore, the copy of processor states maintained by the translation layer?1030?for each non-native guest operating system may comprise two parts, one for the native processor states that may be mapped with the non-native processor states while the other for the extra states representing the non-native processor states that may not be mapped with any of the native processor states.
With reference to FIG. 4, an embodiment of saving/restoring processor states by utilizing the above-stated processor state mapping method will be described under a presumption of switching processes from a guest operating system to another guest operating system. However, it may be appreciated that saving/restoring processor states for a guest operating system may happen as long as stopping or resuming the guest operating system.
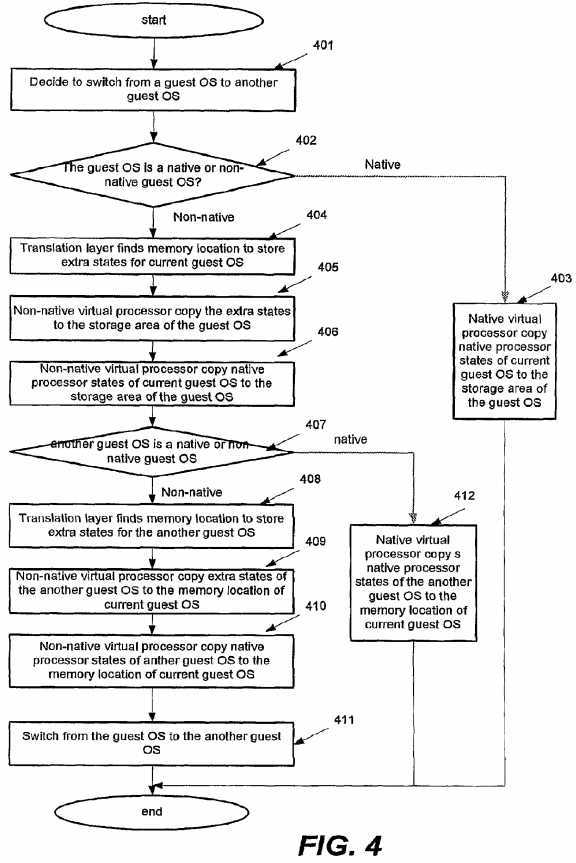
As depicted, in block?401, it may be determined to switch processes from a guest operating system running as a current guest operating system to another guest operating system. Then, in block?402, the virtual machine monitor?100?or other suitable device may determine whether the guest operating system to be stopped is a native guest operating system or a non-native guest operating system. In response to determining that the guest operating system is a native guest operating system, the native virtual processor?104?or other suitable device may copy native processor states for the current guest operating system to the storage area allocated to store processor states for the guest operating system.
However, in response to determining that the guest operating system is a non-native, the virtual machine monitor?100?may call the translation layer?1030?to find memory location to store extra states for the current operating system in block?404. As stated above, the extra states may represent the non-native processor states that may not be mapped with any of the native processor states. Then, in block?405, the non-native virtual processor?105?or other suitable device may copy the extra states for the current guest operating system to the storage area allocated to store processor states for the guest operating system. In block?406, the non-native virtual processor?105?or other suitable device may further copy native processor states for the current operating system to the storage area for the guest operating system. As stated above, the native processor states may be mapped with corresponding non-native processor states.
Then, in block?407, the virtual machine monitor?100?or other suitable device may determine whether the another guest operating system to be resumed is a native or non-native guest operating system. In response to determining that the another guest operating system is a native guest operating system, the native virtual processor?104?may copy native processor states from a storage area allocated to store processor states for the another guest operating system to the memory location for the current operating system.
However, in response to determining that the another guest operating system is a non-native guest operating system, the virtual machine monitor?100?may call the translation layer?1030?to find memory location to store extra states for the another guest operating system in block?408, and the non-native virtual processor105?may copy the extra states for the another guest operating system to the memory area allocated to store processor states for the current operating system in block?409. Then, in block?410, the non-native virtual processor?105?may copy native processor states for the another guest operating system to the memory area for the current operating system.
Finally, in block?411, the virtual machine monitor?100?or other suitable device may switch processes from the guest operating system to the another guest operating system.
An embodiment of translating a non-native physical address into a native physical address by utilizing the translation layer?1030?is depicted in FIG. 5.
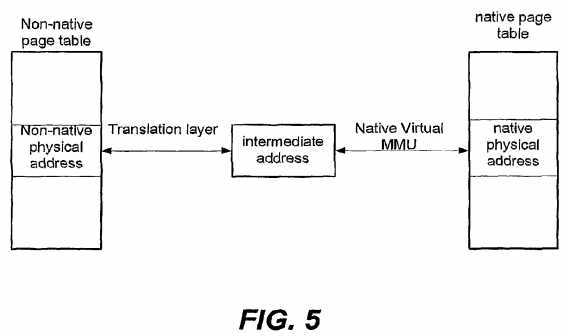
In the embodiment, a non-native guest operating system supporting the non-native guest system architecture may maintain a non-native page table. Each entry of the non-native page table may store a non-native physical address of each non-native memory page. Accordingly) the translation layer?1030?or other suitable device may maintain a native page table mappable with the non-native page table, wherein each entry of the native page table may store a native physical address of a native memory page complying with the host system architecture. Examples for the non-native page table may comprise virtual hashing page table (VHPT) for a 32-bit system architecture and examples for the native page table may comprise LVHPT (long-format VHPT) for a 64-bit system architecture. In order to translate the non-native physical address into the native physical address, the translation layer?1030?may generate an intermediate address complying with the host system architecture based upon the non-native physical address and the native virtual MMU?106?may translate the intermediate address into the native physical address by looking on the intermediate address as a native logical address.
Other embodiments may implement other technologies for address translation as shown in FIG. 5. For example, the translation layer?1030?may translate the non-native physical address into native physical address without the aid of the intermediate address. For another example, the translation layer?1030?may complete the address translation independently instead of depending upon the native virtual MMU?106.
FIG. 6 depicts an embodiment of the intermediate address given that the non-native guest system architecture is a 32-bit architecture and the host system architecture is a 64-bit architecture. However, it should be appreciated that structure of the intermediate address may vary under different system architectures.
The upper part of FIG. 6 shows a data structure of a native logical address supporting the host system architecture, i.e., 64-bit system architecture. The top three bits of the 64-bit logical address (bits?61-63), i.e., virtual region number, may be used to index into an array of eight region registers maintained by the native virtual MMU, yielding a region ID. The remaining bits of the 64-bit logical address may form a virtual page number and an offset. The 64-bit system architecture may support sharing of translation lookup buffer (TLB) entries on a region basis, for example, the TLB may find corresponding physical page number based upon the region ID and virtual region number, which may result a 64-bit physical address formed of the physical page number and the offset in the 64-bit logical address. However, the non-native guest system architecture, i.e., 32-bit system architecture, may support address translation on a segmented basis. In other words, a logical address supporting the 32-bit system architecture may consist of a segment identifier and an offset, while the segment identifier is a 16-bit field called segment selector, and the offset is a 32-bit field. Under the 32-bit system architecture, the translation from the logical address into a 32-bit physical address may start from retrieving the segment selector from the logical address.
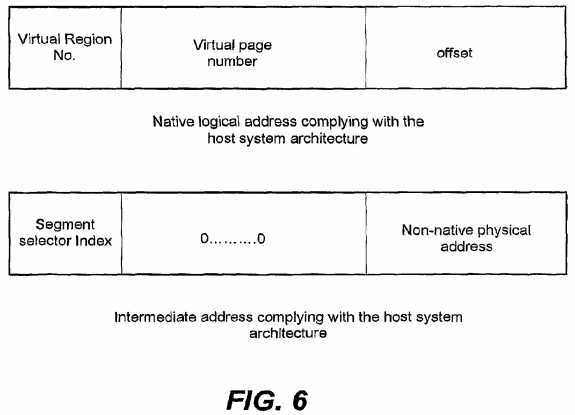
In view of above, the translation layer?1030?may generate an intermediate address under the 64-bit system architecture as depicted in the under part of FIG. 6. The translation layer?1030?may emulate the segmentation complying with 32-bit architecture with the region complying with 64-bit architecture, namely, different segment selectors may be represented by different regions and different segment selectors (cs:ds:fs:gs:es:ss) may be indexed with different virtual region numbers?0-5. Therefore, the top three bits of the intermediate address may present segment selector index?0-5?as virtual region number.
Further, the translation layer?1030?may embed the 32-bit physical address into one of the virtual page number and the offset of the 64-bit logical address and zero the other, resulting the intermediate address with 64-bits value following the 64-bit system architecture.
FIG. 7 depicts an embodiment of a method of updating a non-native page table maintained by a non-native guest operating system with use of the address translation of FIGS. 5-6. However, it should be appreciated that the address translation may be adopted in other applications besides updating the non-native page table.
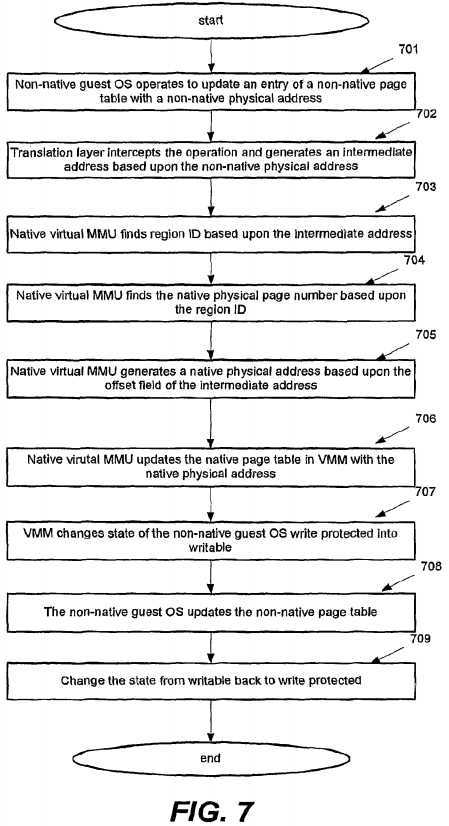
In block?701, the non-native guest operating system supporting the non-native guest system architecture may operate to update an entry of a non-native page table with a non-native physical address. In block?702, the translation layer?1030?may intercept the operation when the non-native guest operating system tries to access the control register where the translation layer?1030?may have the privileged right to access. The translation layer?1030?may then generate an intermediate address complying with the host system architecture based upon the non-native physical address complying with the non-native guest system architecture.
In block?703, the native virtual MMU?106?may obtain a region?10?by retrieving the virtual region number from the intermediate address and then find a physical page number based upon the region ID and virtual page number in the intermediate address in block?704.
Then, in supporting the host system architecture block?705, the native virtual MMU?106?may generate a native physical address complying with the host system architecture based upon the physical page number obtained in block?704?and the offset field of the intermediate address. In block?706, the native virtual MMU?106may update a native page table maintained in the virtual machine monitor?100?for the non-native guest operating system with the generated native physical address. It can be seen that the native page table in the virtual machine monitor?100?may correspond to the non-native page table in the non-native guest operating system, wherein each non-native physical address stored in the non-native page table mappable with each native physical address stored in the native page table.
In block?707, the virtual machine monitor?100?or other suitable device may change a page table state for the non-native guest operating system from write protected state into writable state so that the non-native guest operating system may update the entry of the non-native page table with the non-native physical address in block?708. Finally, in block?709, the virtual machine monitor?100?or other suitable device may change the page table state back into write protected state, so that any future operations of updating the non-native page table by the non-native guest operating system may be intercepted again.
Other embodiments may implement other technologies for address translation as shown in FIG. 7. For example, the translation layer?1030?may be able to translate the non-native physical address into native physical address with the aid of the intermediate address in other structures or without the aid of the intermediate address at all. In such case, blocks?702-705?for generating the native physical address may be modified accordingly. For another example, if the non-native guest system architecture and host system architecture are different from 32-bit and 64-bit system architectures, blocks?702-705?may be modified accordingly
FIG. 8A shows an embodiment of translating a non-native I/O instruction or non-native memory mapped I/O instruction complying with the non-native guest system architecture into native memory mapped I/O complying with the host system architecture.
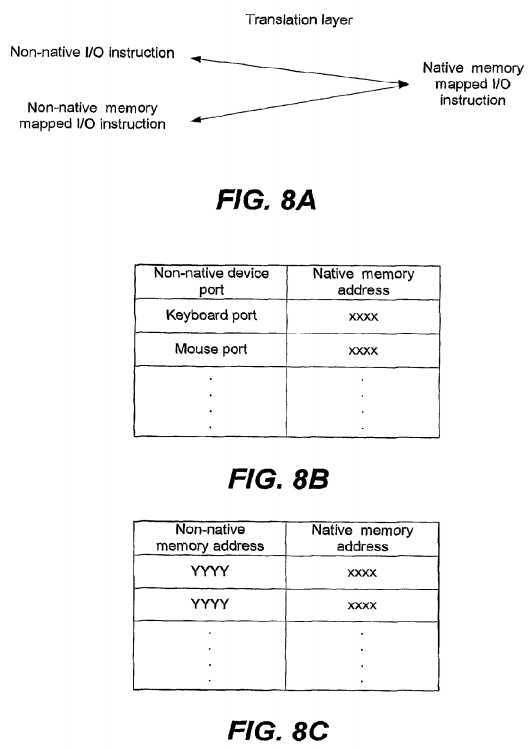
In the embodiment, a special native memory page may be allocated for each non-native guest operating system and store native device ports in its entries. A native memory mapped I/O may be represented by a native memory address of the native page entry storing the native device port. However, the non-native guest operating system may itself maintain a non-native memory page corresponding to the native memory page and the non-native memory mapped I/O may be represented by a non-native memory address of the non-native page entry storing the non-native device port.
The non-native guest operating system may perform a device related I/O operation by executing a non-native instruction such as a non-native I/O instruction or a non-native memory mapped I/O instruction, wherein the non-native I/O instruction may comprise a non-native device port number while the non-native memory I/O instruction may comprise a non-native memory address of an entry in the non-native memory page storing the non-native device port number. The translation layer?1030?may intercept the non-native instruction from the non-native guest operating system and translate the non-native instruction into the native memory mapped I/O instruction complying with the host system architecture. For the non-native I/O instruction, the translation layer?1030?may extract the non-native device port number from the instruction, and translate the non-native device port number into the native memory address storing the corresponding native device port number with reference to a port-address table maintained by the native virtual device?107. FIG. 8B shows an example of the port-address table. The table may comprise two columns, one for the non-native device port number and the other for the native memory address. For the non-native memory mapped I/O instruction, the translation layer?1030?may extract the non-native memory address from the instruction, and translate the non-native memory address into the native memory address storing the corresponding native port number with reference to an address-address table maintained by the native virtual device?107. FIG. 8C shows an example the address-address table. The table may comprise two columns, one for the non-native memory address and the other for the native memory address.
FIG. 9 shows an embodiment of a method of servicing an I/O operation for a non-native guest operating system in the heterogeneous virtualization platform of FIG. 1.
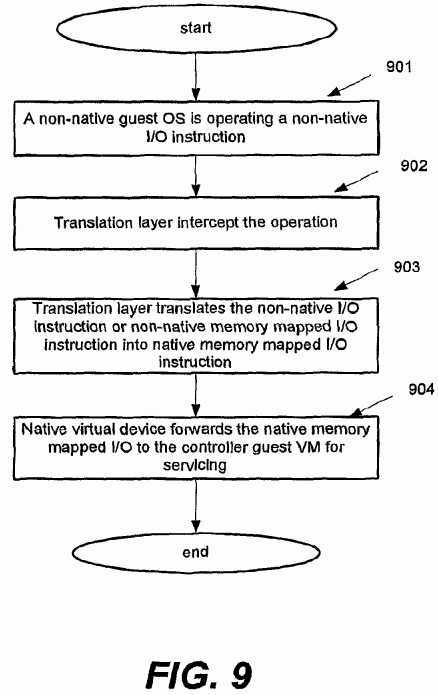
In block?901, the non-native operating system supporting the non-native guest system architecture is executing a non-native instruction for a device related?110?operation, for example, input/output data to/from a device. In block?902, the translation layer?1030?operating in a privileged level may intercept the non-native instruction from the non-native guest operating system since the non-native guest operating system is de-privileged. Then, the translation layer?1030?may translate the non-native instruction into the native memory mapped I/O instruction in block?903. The translation may vary in accordance with the non-native instruction in different forms, e.g., non-native I/O instruction or non-native memory mapped I/O instruction, as stated above with reference to FIGS. 8A-8C.
The heterogeneous virtualization platform may comprise a plurality of guest virtual machines, one of which may be a controller guest virtual machine responsible for managing device related I/O operations in other guest virtual machines. In this context, the native virtual device?107?may forward the native memory mapped I/O to the controller guest virtual machine for I/O servicing in block?904.
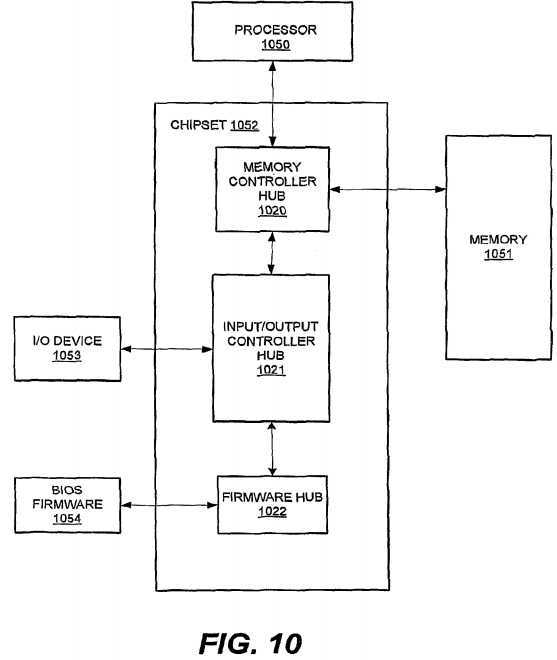
FIG. 10 depicts an embodiment of a general computer system implementing the heterogeneous virtualization as shown in FIG. 1. The computing platform may comprise one or more processors?1050, memory?1051, chipset?1052, I/O device?1053, BIOS firmware?1054?and possibly other components. The one or more processors?1050?are communicatively coupled to various components (e.g., the memory?1051) via one or more buses such as a processor bus. The processors?1050?may be implemented as an integrated circuit (IC) with one or more processing cores that may execute codes complying with a host system architecture, for example, including Intel? Xeon?, Intel? Pentium?, Intel? Itanium? architectures, available from Intel Corporation of Santa Clara, Calif.
In an embodiment, the memory?1051?may store codes to be executed by the processor?1050. A non-exhaustive list of examples for the memory?1051?may comprise one or a combination of the following semiconductor devices, such as synchronous dynamic random access memory (SDRAM) devices, RAMBUS dynamic random access memory (RDRAM) devices, double data rate (DDR) memory devices, static random access memory (SRAM), flash memory devices, and the like.
In an embodiment, the chipset?1052?may provide one or more communicative path among the processor?1050, memory?1051?and various components, such as the I/O device?1053?and BIOS firmware?1054. The chipset?1052?may comprise a memory controller hub?1020, an input/output controller hub?1021?and a firmware hub?1022.
In an embodiment, the memory controller hub?1020?may provide a communication link to the processor bus that may connect with the processor?1050?and to a suitable device such as the memory?1051. The memory controller hub?1020?may couple with the I/O controller hub?1021?that may provide an interface to the I/O devices?1053?for the computing platform such as a keyboard and a mouse. A non-exhaustive list of examples for the I/O devices?1053?may comprise a keyboard, mouse, network card, a storage device, a camera, a blue-tooth, an antenna, and the like.
In an embodiment, the memory controller hub?1020?may communicatively couple with a firmware hub?1022?via the input/output controller hub?1021. The firmware hub?1022?may couple with the BIOS firmware?1054?that may store routines that the computing platform executes during system startup in order to initialize the processors?1050, chipset?1052, and other components of the computing platform. Moreover, the BIOS firmware?1054?may comprise routines or drivers that the computing platform may execute to communicate with one or more components of the compute platform.
The computer system as depict in FIG. 10 may perform as the computer system?1000?as depicted in FIG. 1. The memory?1051?may store software images as a virtual machine monitor including the control interface?101, the native service virtual machine?102, the non-native service virtual machine?103?including the translation layer?1030, the native virtual processor?104, the non-native virtual processor?105, the native virtual MMU?106?and the native virtual device?107, and possibly other components. The memory?1051?may further store guest software including guest operating system and guest applications.
Other embodiments may implement other technologies for the structure of the computer platform as shown in FIG. 10. For example, the memory controller hub?1020?may be embedded into the processor?1050?by providing a processor containing on-die memory controller
SRC=http://www.freepatentsonline.com/8645951.html
PatentTips - Supporting heterogeneous virtualization,布布扣,bubuko.com
PatentTips - Supporting heterogeneous virtualization
标签:des style blog code http tar
原文地址:http://www.cnblogs.com/coryxie/p/3793575.html