标签:des style class blog code http
最近在学习check_mk,这是一款基于nagios监控工具,但比nagios更易使用,引起了我的兴趣,我最关注的依然是对自定义监控脚本的支持度。在windows下的实践,其支持的客户端脚本或插件可以是 exe,bat,vbs,ps1等,我采用powershell来编写监控脚本。
本文适合对check_mk有一定了解的人,关于check_mk的介绍和搭建,请点击查看:手把手打造开源新监控利器check_mk
另外如果觉得这篇文章描述不够清晰,可以参考官方文档:http://mathias-kettner.de/checkmk_devel_agentbased.html
=====================================================================================================
1、首先我们在客户端创建自定义监控脚本 process_top5.ps1:
$dp = (Get-Process) | select -First 5 echo `<`<`<process_top5`>`>`> #这个输出很重要,用来告诉check_mk监控端目标客户端有哪些监控项 foreach($p in $dp){ Write-Host $p.name $p.WorkingSet }
脚本很简单,抓取当前计算机前5个进程,输出进程名和内存占用。将这个文件拷贝到 客户端check_ck插件目录(C:\Program Files (x86)\check_mk\plugins)
2、在监控端输入“check_mk -d hostname”,查看返回内容中可以看到<<<process_top5>>>段,可以看到有5项进程信息
[[[Windows PowerShell]]] <<<logwatch>>> <<<process_top5>>> agent 19939328 AlipaySecSvc 20549632 aspnet_state 1511424 check_mk_agent 9351168 cmd 6447104 <<<local>>>
现在需要在监控端 编写check脚本,用于解析客户端返回值,检查项脚本位于“/usr/share/check_mk/checks”目录下(check脚本为python编写,需要些的东西并不负责,所以不会python的人也无需担心)。注意文件名必须和新增的监控项名相同(即process_top5),内容如下:
process_top5_default_values=(10000000,15000000) #定义报警阈值,顺序无所谓 #inventory代表检查清单,参数info为客户端返回项<<<process_top5>>>,其返回值inventory用于check_process_top5中的item参数 def inventory_process_top5(info): inventory = [] for line in info: disk = line[0] field = int(line[1]) inventory.append( (disk, "process_top5_default_values") ) return inventory #这个是check主函数 def check_process_top5(item,params,info): warn,crit = params #取出process_top5_default_values中定义的阈值,注意赋值顺序,这里warn取值10000000,crit取值15000000 for line in info: if (line[0]) == item : celsius = int(line[1]) if celsius > crit: return (2, "mem is %d" % celsius) elif celsius > warn: return (1, "mem is %d" % celsius) else: return (0, "mem is %d" % celsius) return (3, "%s not found in agent output" % item) #这里是向check_mk添加检查项 check_info["process_top5"] = { ‘check_function‘: check_process_top5, ‘inventory_function‘: inventory_process_top5, ‘service_description‘: ‘%s‘, }
3、 通过“ check_mk -L | grep process_top5” 可以看到监控端已经有该check,然后要将process_top5添加到对应的host文件上
[root@trdcentos62 ~]# check_mk --checks=process_top5 -I [hostname] process_top5 5 new checks
“5 new checks”代表process_top5新增了5个监控项,实际上就是对应的5个进程项,在该host对应autocheck文件也已经增加了这5项,如下
[root@trdcentos62 ~]# cat /var/lib/check_mk/autochecks/3.81.mk [ ("3.81", "process_top5", ‘AlipaySecSvc‘, process_top5_default_values), ("3.81", "process_top5", ‘agent‘, process_top5_default_values), ("3.81", "process_top5", ‘aspnet_state‘, process_top5_default_values), ("3.81", "process_top5", ‘check_mk_agent‘, process_top5_default_values), ("3.81", "process_top5", ‘cmd‘, process_top5_default_values), (‘3.81‘, ‘df‘, ‘C:/‘, {}), (‘3.81‘, ‘df‘, ‘D:/‘, {}), (‘3.81‘, ‘df‘, ‘E:/‘, {}), (‘3.81‘, ‘df‘, ‘F:/‘, {}), (‘3.81‘, ‘df‘, ‘G:/‘, {}), (‘3.81‘, ‘logwatch‘, ‘HardwareEvents‘, ""), (‘3.81‘, ‘logwatch‘, ‘Windows PowerShell‘, ""), (‘3.81‘, ‘mem.win‘, None, {}), (‘3.81‘, ‘uptime‘, None, {}), (‘3.81‘, ‘winperf_if‘, ‘01‘, {‘state‘: [‘1‘], ‘speed‘: 1000000000}), (‘3.81‘, ‘winperf_if‘, ‘02‘, {‘state‘: [‘1‘], ‘speed‘: 1000000000}), (‘3.81‘, ‘winperf_if‘, ‘03‘, {‘state‘: [‘1‘], ‘speed‘: 1000000000}), (‘3.81‘, ‘winperf_if‘, ‘04‘, {‘state‘: [‘1‘], ‘speed‘: 1000000000}), (‘3.81‘, ‘winperf_if‘, ‘05‘, {‘state‘: [‘1‘], ‘speed‘: 100000}), (‘3.81‘, ‘winperf_if‘, ‘06‘, {‘state‘: [‘1‘], ‘speed‘: 100000}), (‘3.81‘, ‘winperf_if‘, ‘07‘, {‘state‘: [‘1‘], ‘speed‘: 100000}), (‘3.81‘, ‘winperf_if‘, ‘08‘, {‘state‘: [‘1‘], ‘speed‘: 100000}), (‘3.81‘, ‘winperf_if‘, ‘09‘, {‘state‘: [‘1‘], ‘speed‘: 1410065408}), (‘3.81‘, ‘winperf_if‘, ‘10‘, {‘state‘: [‘1‘], ‘speed‘: 100000}), (‘3.81‘, ‘winperf_phydisk‘, ‘SUMMARY‘, diskstat_default_levels), (‘3.81‘, ‘winperf_processor.util‘, None, winperf_cpu_default_levels), ]
4、打开check_mk监控页面,查看对应host的service,可以看到已经增加的那5项信息
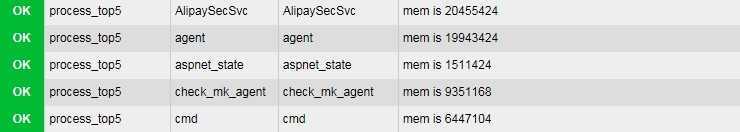
check_mk自定义监控实践之powershell,布布扣,bubuko.com
标签:des style class blog code http
原文地址:http://www.cnblogs.com/waiwofei/p/3810544.html