标签:
Instrusion Detection System (IDS) is a security control or countermeasure that has the capability to detect misuse and abuse of, and unauthorized access to, network resources.
Instrusion Prevention System (IPS) is a security control or countermeasure that has the capaility to detect and prevent misuse and abuse of, and unauthorized access to, netwrok resources.
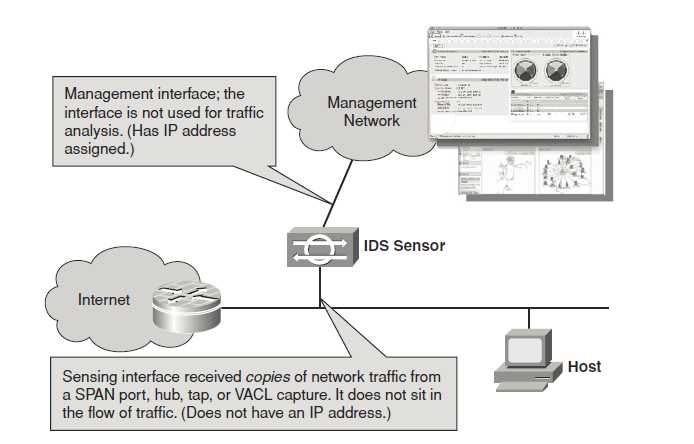
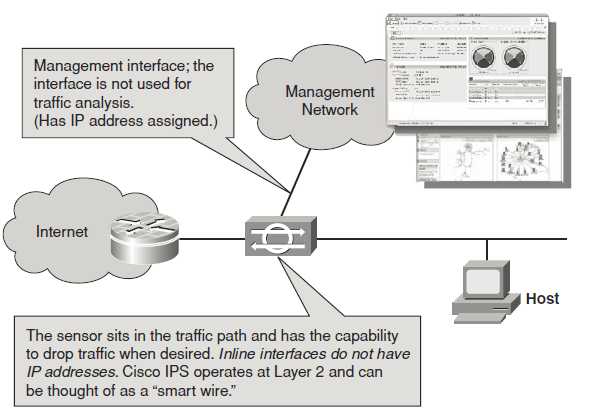
Some of the most commonly detected attacks by networks IDS are as follows:
After an IDS detects an anomaly or offending traffic, it generaes alerts. An IDS cannot stop an attack or malicious traffic along.
Security controls are classified in one of the following terms:
True positive: A situation in which a signature fires correctly when intrusive traffic for that signature is detected on the network. The signature correctly identifies an attack against the netwrok. This represents normal and optimal operation.
False positive: A situation in which normal user activity triggers an alarm or response. This is a consequence of nonmailcious activity. This represents an error and generally is caused by excessively tight proactive controls or excessively relaxed reactives controls.
Ture negative: A situation in which a signature does not fire during normal user traffic on the network. The securirty control has not acted and there was no malicious activity. This represents normal and optimal operation.
False negative: A situatoin in which a detection system fails to detect instrusive traffic although there is a signature designed to catch the activity. In this situation, there was malicious activity, but the security control did not act. This represents an error and generally is caused by excessively relaxed proactive controls or excessively tight reactive controls.
A vulnerability is a weakness that compromises either the security or the functionality of a system. You‘ll often hear the following examples listed as vulnerabilitys:
An exploit is the mchanism used to leverge a vulnerability to compromise the security functionality of a system.
A threat is defined as any circumstance or event with the expressed potential for the occurrence of a harmful event to an information system in the form of destruction, disclosure, adverse modification of data, or DoS.
A risk is the likelihood that a particular threat using a specific attack will exploit a particular vulnerability of an asset or system that results in an undesirable consequence.
There are different aspects in which a network IPS analyzes traffic, such as following:
There are three commonly used approaches to network instrusion prevention by security manages today:
Endpoint Security Controls
Host IPS(HIPS) is another form of instrusion prevention. consists of operating system security controls or security agent software installed on hosts that can include desktops PCs, laptops, or servers.
标签:
原文地址:http://www.cnblogs.com/elewei/p/4735088.html